Nikto Cheat Sheet
- Nikto Scan Cheat Sheet
- Nikto Cheat Sheet Template
- Nikto Cheat Sheet Sans
- Nikto Cheat Sheet Download
- Nikto Cheat Sheet Printable
port scanning
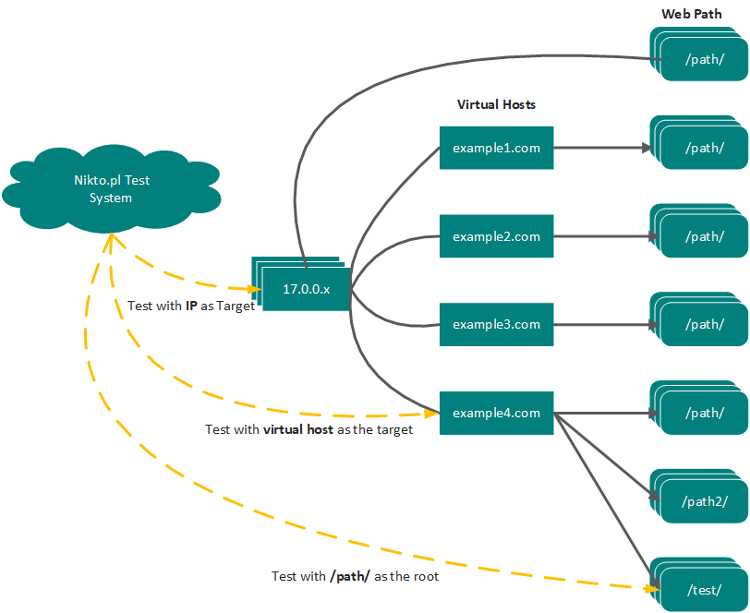
- Perl nikto.pl -h 192.168.1.188 -Cgidirs all -o test -Format csv The 'all' options would instruct Nikto2 to test all available CGI directories. If you want to specify a specific CGI directory, the.
- JustTryHarder, a cheat sheet which will aid you through the PWK course & the OSCP Exam. (Inspired by PayloadAllTheThings) Feel free to submit a Pull Request & leave a star to share some love if this helped you.
Ubuntu Commands: A Cheat Sheet With Examples By Nicholas Brown – Follow me on Twitter. There are numerous useful Ubuntu Linux commands at your disposal, and they actually make life easier in some cases. If the help menu is confused, you are welcome to use Nikto cheat sheet. This is one of the examples. Task 2-1: Flag for scanning a host There are two answers to this question.
Nmap
Network exploration tool and security/ port scanner
Unicornscan
A port scanner that utilizes its own userland TCP/IP stack, which allows it to run asynchronous scans. It can scan 65,535 ports in a relatively short time frame.
Netcat
Netcat might not be the best tool to use for port scanning, but it can be used quickly. While Netcat scans TCP ports by default it can perform UDP scans as well.
1.1.3 TCP Scan
For a TCP scan, the format is:
1.1.4 UDP Scan
For a UDP Port Scan, we need to add -u flag which makes the format:
Amap - Application mapper
identify which services are running on a given port
DNS enumeration
DNS Server
If the targeted machine is running a DNS Server and we have a possible domain name, we may try to figure out A, MX, AAAA records or try zone-transfer to figure out other possible domain names.
Example:
SSL Certificate
If the targeted machine is running an https server and we are getting an apache default webpage on hitting the https://IPAddress, virtual hosts would be probably in use. Check the alt-dns-name on the ssl-certificate, create an entry in hosts file (/etc/hosts) and check what is being hosted on these domain names by surfing to https://alt-dns-name.
nmap service scan result for port 443 (sample)
Scanning Structure
Google-Vulns
It is suggested that whenever you are googling something, you add words such as vulnerability, exploit, ctf, github, python, tool etc. to your search term. For example. Let’s say, you are stuck in a docker or on a specific cms search for docker ctf or <cms_name> ctf/ github etc.
Webservices
Utilize whatweb to find what software stack a server is running.
1.3.3 nikto
nikto - Scans a web server for known vulnerabilities.
It will examine a web server to find potential problems and security vulnerabilities, including:
- Server and software misconfigurations
- Default files and programs
- Insecure files and programs
- Outdated servers and programs
1.3.4 dirb, wfuzz, dirbuster
Furthermore, we can run the following programs to find any hidden directories.
- DIRB is a Web Content Scanner. It looks for existing (and/ or hidden) Web Objects. It basically works by launching a dictionary based attack against a web server and analysing the response.
- wfuzz - a web application bruteforcer. Wfuzz might be useful when you are looking for webpage of a certain size. For example: Let’s say, when we dirb we get 50 directories. Each directory containing an image. Often, we then need to figure out which image is different. In this case, we would figure out what’s the size of the normal image and hide that particular response with wfuzz.
- Dirbuster : DirBuster is a multi threaded java application designed to brute force directories and files names on web/ application servers.
- gobuster : Gobuster is a tool used to brute-force URIs (directories and files) in web sites and DNS subdomains (with wildcard support). (golang can be installed using apt-get).
1.3.5 BurpSuite Spider
There will be some cases when dirb/ dirbuster doesn’t find anything. This happened with us on a Node.js web application. Burpsuite’s spider helped in finding extra-pages which contained the credentials.
1.3.6 PUT Method
Sometimes, it is also a good idea to check the various HTTP verbs that are available such as GET, PUT, DELETE, etc. This can be done by making an OPTIONS request.Curl can be used to check the available options (supported http verbs):
The PUT method allows you to upload a file which can help us to get a shell on the machine. There are multiple methods available for uploading a file with the PUT method mentioned on Detecting and exploiting the HTTP Put Method
A few are:
- Nmap:
- curl:
or
1.3.7 Wordpress
When faced with a website that makes use of the wordpress CMS one can run wpscan. Make sure you run –enumerate u for enumerating usernames because by default wpscan doesn’t run it. Also, scan for plugins
We can also use wpscan to bruteforce passwords for a given username
Secploit Terminal Search Engine
it is web tool made to make it easy to query search using tags search or with exploit name
or we can search for specific vulnerability on specific software easily ,using tags support
searchsploit
Exploit Database offline Archive Search for vulnerable software , shells , papers
Once we have figured out which exploit to check we can read about it by using the file-number. For example: 1997, 2017, 24574 in the above case.
Searchsploit provides an option to read the nmap XML file and suggest vulnerabilities (Requires nmap -sV -x xmlfile).
PHP Web Shell
or
or
which can then be accessed by
If there’s a webpage which accepts phpcode to be executed, we can use curl to urlencode the payload and run it.
- PHP Meterpreter
We can set the multi-handler in metasploit by
PHP Reverse Shell
The code below assumes that the TCP connection uses file descriptor 3. This worked on my test system. If it doesn’t work, try 4 or 5 or 6.
Ruby
Perl
Python
TCP
UDP
Java
JSP
Bash
If a server (attacker machine) is listening on a port:
then we can use the below to connect
Method 1:
Method 2:
Method 3:
Telnet Reverse Shell
XTerm
To catch the incoming xterm, start an X-Server:
You’ll need to authorize the target to connect to you (command also run on your host):
Lynx
MYSQL
- If we have MYSQL Shell via sqlmap or phpmyadmin, we can use mysql outfile/ dumpfile function to upload a shell.
or
- If you have sql-shell from sqlmap/ phpmyadmin, we can read files by using the load_file function.
Reverse Shell from Windows
Executable Meterpreter Payloads
Secploit Online reverse Shells Generator
you can also generate any type by choosing bash or python , ruby ..etc
Everyone knows: cheat sheets are cool! They are very useful if you already know the basics about a topic but you have to look up details when you are not sure about something.
Especially, if you are new to a certain topic and you have to learn a lot of new stuff, it’s sometimes very hard to memorize everything.
Imagine you just got your 1st job as a security analyst. You’ll have to learn a lot of new tools, command options, attacks and so on. How can you quickly do a reverse DNS lookup of every IP address in a network? How can you run a specific nmap script against all servers on port 23? How do you show the details of a certificate of a TLS service? How did this Metasploit payload generation tool work again? How was this logonpasswords command called in mimikatz? And how again can I reuse relayed NTLM sessions using SOCKS? OK, I think you got it – it’s not so easy, right?
That’s exactly the place where cheat sheets come in handy!

So, I created a cheat sheet that contains lots of commands and tools that we often use during our penetration tests, security assessments or red teaming engagements. The cheat sheet contains info about the following topics:
- Basic Linux Networking Tools (ip, dig)
- Information Gathering (whois, CT logs, subdomain enumeration)
- TCP Tools (ncat)
- TLS Tools (openssl, ncat, sslyze, socat)
- HTTP Tools (python webserver, curl, nikto, gobuster)
- Sniffing (ARP spoofing, tcpdump, Wireshark, …)
- Network Scanning (nmap, masscan)
- Shells (Bind/reverse shells)
- Vulnerability DBs and Exploits (searchsploit and some links)
- Cracking (ncrack, hashcat, John the Ripper)
- Metasploit Framework (Use exploits, generate shells, shell listeners, meterpreter, pivoting, SOCKS proxying)
- Linux Privilege Escalation (LinEnum, lynis, GTFOBins)
- Windows Privilege Escalation (PowerSploit, smbmap)
- Windows Credentials Gathering (mimikatz, lsadump)
- Passh-The-Hash (Lots of impacket tools)
- NTLM Relay (ntlmrelayx, SOCKS proxying)
- Active Directory (BloodHound & PingCastle)
- Online References
Nikto Scan Cheat Sheet
The cheat sheet can be found here:
Download as a handy printable PDF:
Grab it while it’s hot 🤘!
Nikto Cheat Sheet Template
Note: The latest version can always be found on GitHub: https://github.com/CompassSecurity/Hacking_Tools_Cheat_Sheet
Nikto Cheat Sheet Sans
Do you want to know more about these attack techniques and tools? Then, our new security training “Internal Network and System Security” might be something for you! In this training, the students will learn how attackers find security vulnerabilities in internal networks, how they are exploited and especially how to protect yourself and your infrastructure from such attacks. So this is a perfect course for network and system administrators that want to know the tools of the attackers in order to defend against them.
More infos about this training in general can be found here: https://www.compass-security.com/en/services/security-trainings/course-description-internal-network-and-system-security/.
Nikto Cheat Sheet Download
There is a public training on the 11th and 12th of February 2020 where everyone whoi is interested can participate. More info can be found here: https://www.compass-security.com/en/services/security-trainings/translate-to-english-internal-network-and-system-security-februar-2020-bern/ . Note: This training will be held in German only (slides/course material are in English).
Nikto Cheat Sheet Printable
So, happy hacking and have fun!